Security Tips for Smartphone Users
When it comes to smart-phone security and privacy, people are usually divided into two major camps.
On one side, there are the ones who don’t even care about this issue. They aren’t aware of the potential vulnerabilities they expose themselves to. They can’t imagine why would anyone want to breach into their smart-phone or what can be done with their data. They’ve never even given a thought on how valuable is the data accessible through their phones and what would happen if it got leaked to their business competitors, sold or simply deleted.
Here are some scary statistics that might make them rethink the way they use their phones:
They are convinced that, if you want privacy and security, you can only achieve that either by using a burner, tons of layers of firewalls and proxies, or one of those new (and expensive) phones that focus on strong encryption.

It’s true that lately there’s been a market invasion of phones and apps that promote themselves as enhancers of your protection and security.
While we applaud the initiative, we should also point out that cyber security education is also very important. If you don’t set up some essential security layers, you’ll be extremely vulnerable on any phone you use, no matter its brand or operating system.
What it’s important is that you know how to properly use that phone and create some basic security habits in order not to expose yourself.

After they purchase a new phone, most people don’t even take their time to check all the existent settings.
Yes, it’s a shame that some of them aren’t activated by default. Things like two-factor authentication and automated screen-lock should be imposed by companies, and not offered only as optional settings.
However, basic security settings for smartphones can be tweaked by anyone, without any advanced tech skills, to enforce some much needed security layers.
This is exactly what we plan to show you in this article: an essential list of things that you can do right now in order to keep your smartphone and data safe.
Let’s go!
It’s also essential that you enforce automatic wiping of the device after 10 failed login attempts.
The reason behind this is that you can never know where you’ll accidentally forget your phone and who will end up accessing it. No matter how protective you are with it, there’s no guarantee that it won’t end up stolen one day.
You can simply leave it on your table while in a bar or at work for a quick break, and someone will peek into it. Or, even worse, install a keylogger or screen recorder on it.
Yes, you may currently vouch for your friends and work colleagues and jump into fire for them, but you can never know if that trust is mutual or how your relationship will evolve. Are you willing to take that chance?
Six years ago, I got burned because of my naivety. An employee I had just fired wanted to get revenge, so he hacked into my website and personal accounts and did as much harm as possible. While he was still employed, he managed to install a keylogger on my laptop – laptop I left unattended and without any screen lock on it, thus making all my other security layers useless. Now that I’m looking back at what happened, I feel stupid. Learn from my mistakes!

And now, moving on to the details: don’t use a PIN code for locking the screen. That’s the easiest one to breach, someone just has to be peeking while you unlock your phone.
Instead, treat your screen lock just like you treat any other password: use a unique password, that’s long enough and mixes letters with digits and symbols.
Another option to lock your screen is using a pattern. Choose a complicated one and then deactivate the option that makes it visible when you enter it.
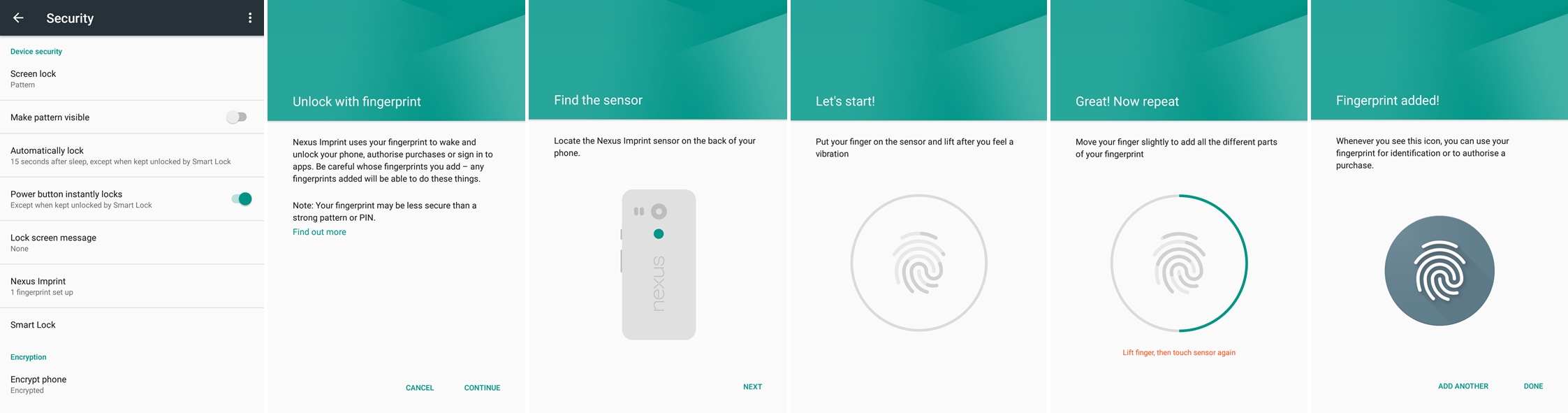
You can also use your fingerprint to wake and unlock your phone, in addition to the pattern, if you have it as an option. Here’s how you set it up in Android (click on the screenshots to enlarge them):
Biometrics are one of the most secure ways of authenticating oneself, and not because of its secrecy, but because it’s so difficult to replicate the data. While we do leave our fingerprints everywhere, it’s much easier for someone to spy on you from behind your shoulder while you enter your PIN than try to replicate your fingerprints.
And looks like biometrics are quickly gaining ground in the mobile world. The company Mastercard is working on a system that will allow us to pay with our faces.
Literally, all we’ll need to do to confirm a payment is take a selfie through a special app and blink while we do it. The blink will be a way to prevent fraud and illegal payments done with our photos, for example. We’ll most likely hear more details about it soon – the due date for starting to implement this option is summer of 2016.

In the same time, security stagnated and just couldn’t keep up. Companies are focused more on marketing than on protecting their user’s data. They don’t care about proactive security and are willing to invest in it only when something bad happens.
Cases of smartphones that got infected with viruses and malware have been on a rise. Some of them ended up with annoying adware, while others were infected with ransomware:
The Apple ecosystem is extremely targeted by cyber crooks, as iPhone owners are considered to be more wealthy and likely to pay a ransom. And because of their centralized system, a security vulnerability can affect a bigger percentage of the users base.
However, devices with iOS are generally considered to be safer than Android because of two main reasons:
1. Market fragmentation: Google allowed every phone manufacturer to personalize its own Android version. While this is also a strength, it’s also harder to control the security for every device that runs on Android, exposing users more to potential bugs.
2. Google is also more permissive with the apps that they allow in their official store. Unlike Apple, Google doesn’t check as thoroughly the apps that they allow users to install.
Of course, this is just a simplified view of the two biggest operating systems existent in the mobile market at this point. They both have their advantages and disadvantages when it comes to cyber security.
What you should keep in mind is that bugs and vulnerabilities will always exist, no matter what operating system you use. What’s important is the way you use it and what privacy layers you enforce.

Here’s what you can do about apps in order to decrease your chances to be infected:
Always use official app stores to download and install an app. Disable the option to allow installation of third party apps. Third party apps usually carry malware that will harm your smartphone. Is that a risk worth taking?
Only install applications that you find in the official app store. That means no apps from third parties – no matter if those third parties are your online buddies, ads, blogs or torrents.
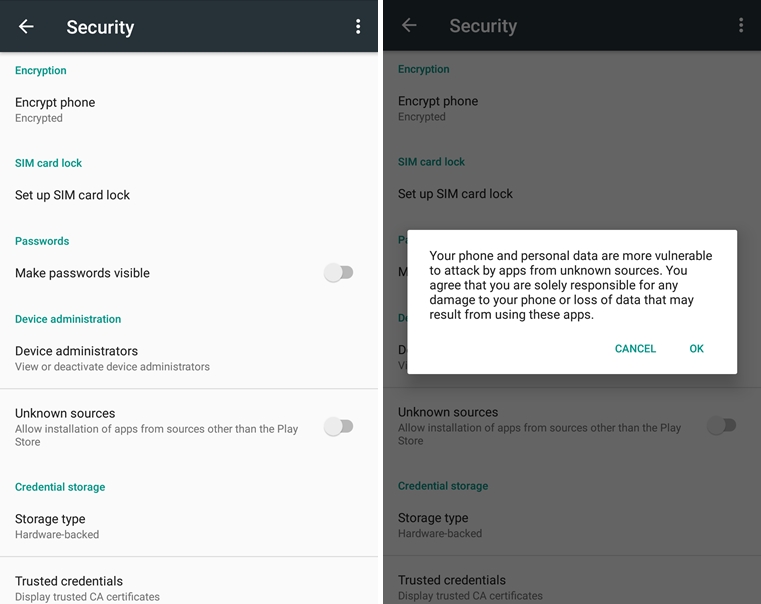
If you have Android, you can disable the option to allow installation of apps from sources other than the Play Store (from Settings -> Security – screenshot below, you can click on it to enlarge it).
However, this doesn’t mean that an app or game from the official store is 100% secure – sometimes, even popular apps, with more than 5 million downloads, can prove to be infected.
Also check the permissions for the installed apps (here’s how to do it). If anything looks out of order, then deny them access to what they’re requesting. A flashlight app doesn’t need permission to access your text messages or contacts, right?
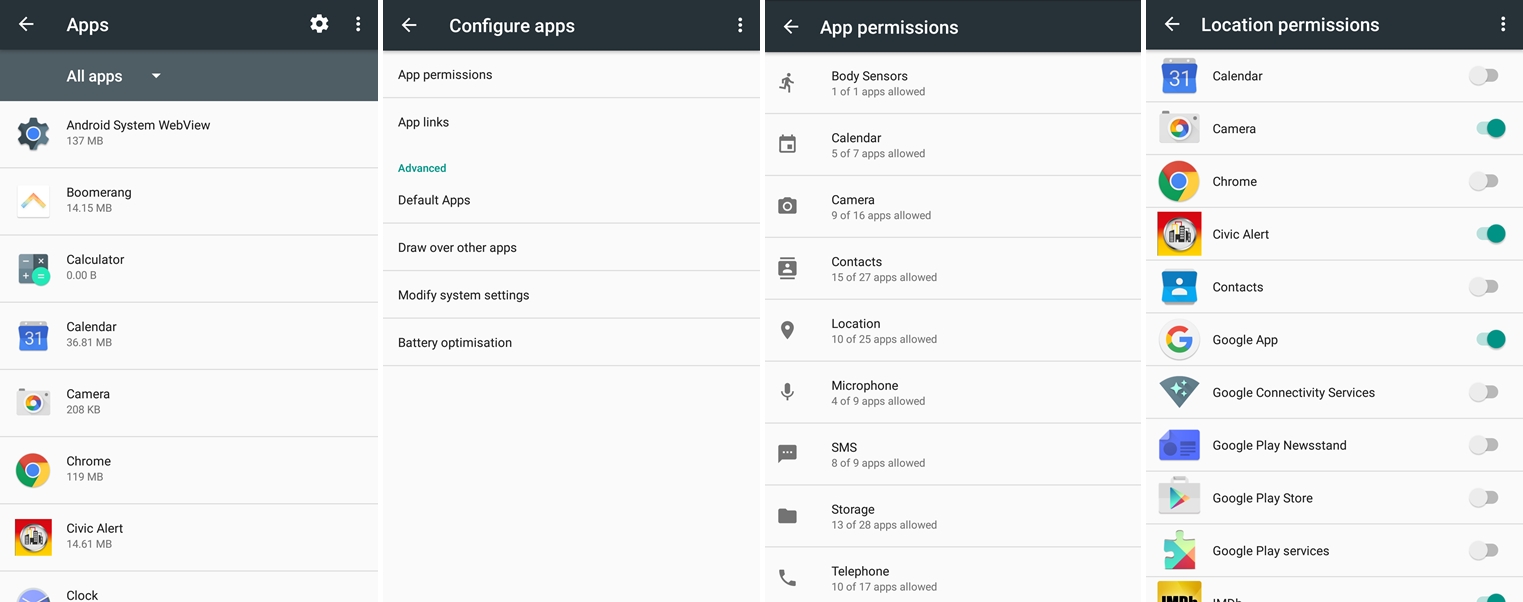
If you have Android, you can go to Settings -> Apps -> App permissions and check exactly what apps required permissions:
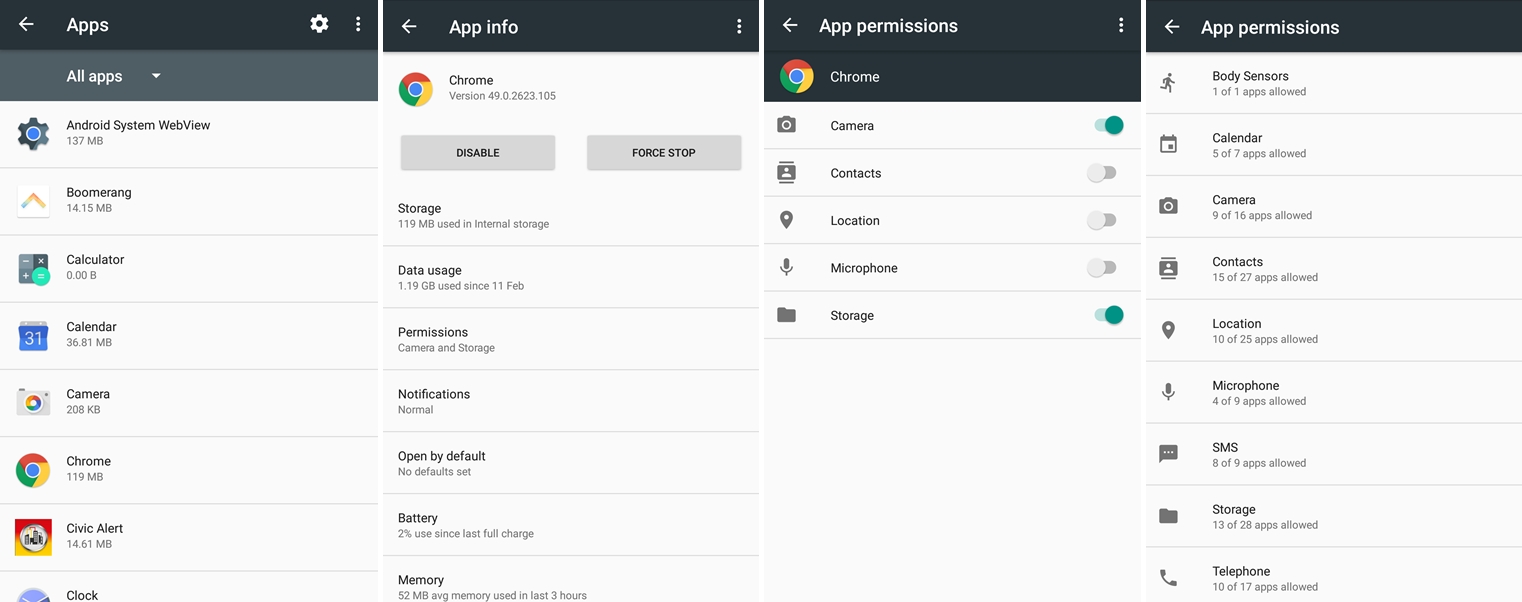
Or you can individually check permissions granted for each app: go to Settings -> Apps and scroll through the list of apps, click on one and individually check what permissions they requested and what you gave them access to:
Or here’s a helpful tool that can ease that task for you: Clueful is a free mobile app developed by Bitdefender that takes a look over what permissions are requested by each app and warns you of the potential threats.
Do a spring cleanup of your apps. Take a look over all the installed apps and remove the ones you’re not using anymore. Those are potential security risks and it’s better to be safe than sorry.
You should also check out the apps that consume the most battery, data or memory, to see if there’s anything suspicious around there. Look for significant changes – this way, you can detect if your smartphone has been compromised.
Update your apps. With each app that remains outdated, including commonplace browsers, your phone is more vulnerable to infections. All it takes is clicking on a link that will redirect you to an infected website – it can be a link from an ad, a spam email, or your friend’s social account that got hacked. Outdated apps leave your data exposed to attacks.
A few weeks ago, a massive Angler malvertising campaign hit major websites, such as The New York Times, BBC, AOL. An ad block software will help decrease your chances of infection.
Blocking pop-ups will also help – you can easily do that from the browser settings. For Chrome, for example, you just have to go to Settings -> Site Settings -> Pop-ups -> and make sure it’s on Blocked.
It’s also recommended that you disable JavaScript for your mobile browser.
This will also help you reduce the data you consume: according to recent studies, ad content is accountable for between 18 to 79% of transferred mobile data. That’s especially true if you navigate through a lot of news websites.

Keep your guard up against phishing on all your devices, no matter if it’s a desktop, laptop, tablet or smartphone. No clicking on short, suspicious links, that you didn’t request. And be careful with those attachments you download via email or instant messaging services.
Cyber attackers can use phishing techniques to withdraw money from you, steal your identity, open credit card accounts in your name and much more. Not even the strongest antivirus will protect you from phishing and malware.
A recent mobile threat is Mazar BOT – a virus that our team detected back in February. It’s spread via links sent in text messages and can give an intruder administrator rights on the victim’s phone. This allows the attackers to read, send and receive SMS, call people, and even erase the phone.
That’s why it’s important that you don’t click on links that you never requested and don’t know where they lead (especially short, hidden links). If somehow you end up clicking on them and they require you to sign-in, don’t give away your credentials.
Do you remember the Fappening, the huge scandal from the summer of 2014? Lots of pics (especially naked ones) with celebrities were stolen from their phones and leaked online. One of the attackers involved pleaded guilty for the attack. His method to access celebrities’ phones? Plain old email phishing:

For iOS there’s the tracking solution called “Find my iPhone”, Microsoft has “Find my phone”, and Android has “Android Device Manager”.
Here’s how Android Device Manager looks like:
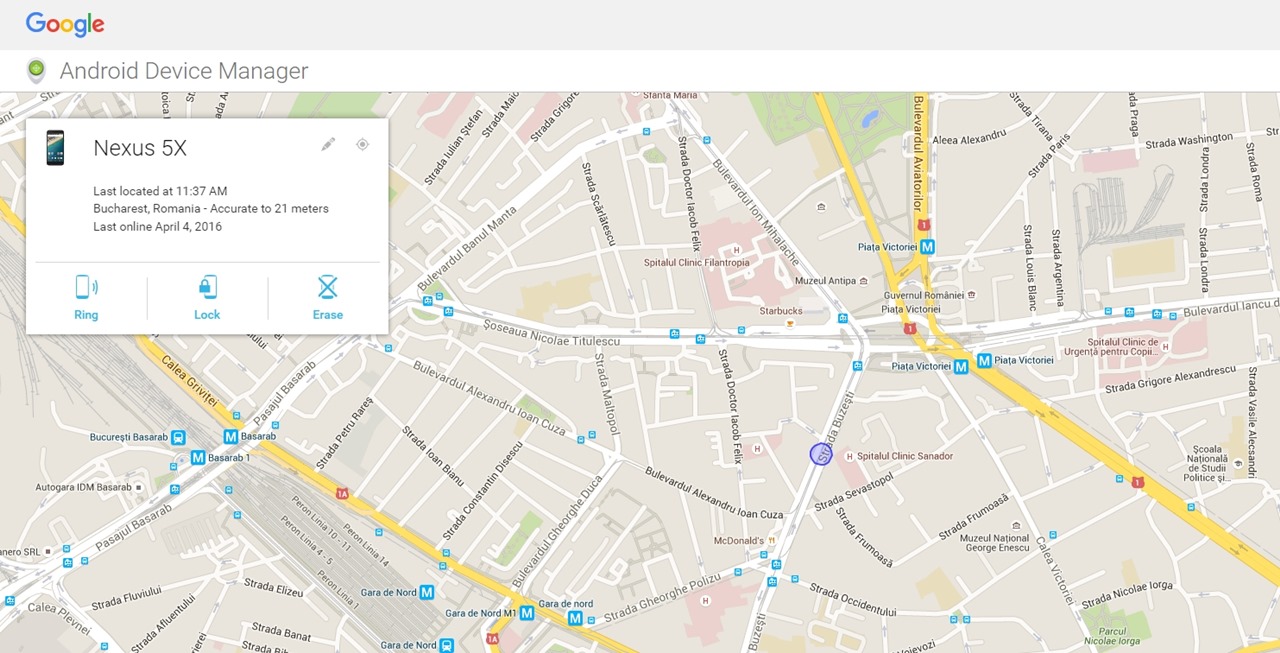
This option is available on all operating systems, you just have to enable it (or don’t disable it, in case it’s already set as default).
In case that your phone is lost, destroyed or stolen, you won’t have to worry about the fact that you didn’t get the chance to backup all your data on it. All apps and data will be automatically synchronized in the cloud.
Here’s how you activate backup in Android (to backup your Photos you’ll have to go in the Photos app and configure it separately – you can choose what folders to backup and at what size to upload the photos):
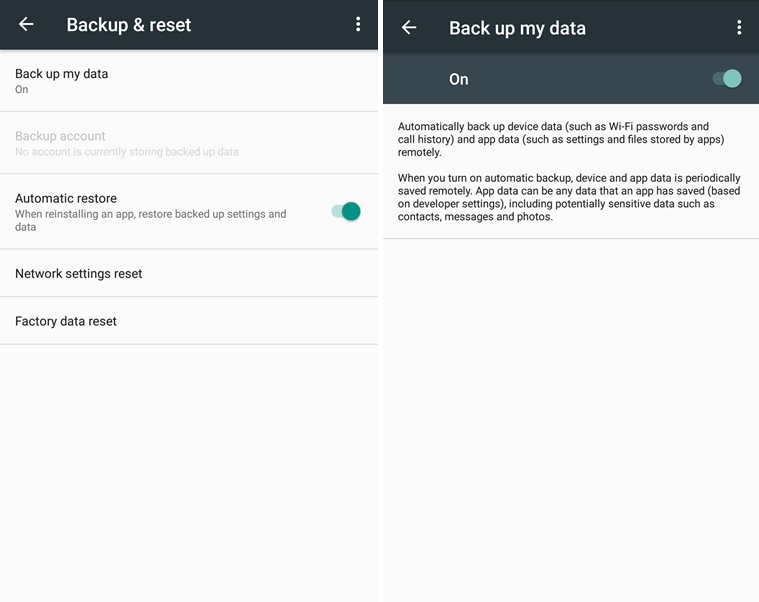
When you’ll set up a new device, you’ll just have to enter the credentials for your Apple or Google account, and all apps, settings and data will be automatically restored.
You can also set up your data to automatically backup in other accounts, such as Dropbox.
If you don’t want to quickly exhaust the internet traffic included in your data plan, set it up to backup only when it connects to wi-fi.
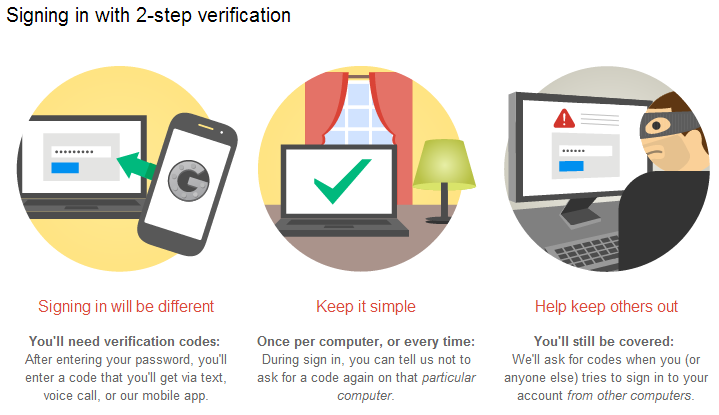
This will act as a second layer of security. Every time you’ll want to sign in on a new device or from a new location, it will require you to verify your identity through a unique, time sensitive code, that you’ll receive via text message.
In case you travel a lot and your phone is unavailable, you’ll be able to use backup codes instead. These are codes that you can use only one time.
Yes, it’s important that you use different passwords for all your accounts. However, in case that someone manages to steal your phone, access it and find out your password, they won’t be able to get through this second step of authentication.
Google explains how encryption works for Android:
Unfortunately, the option to encrypt your data is available for a limited number of operating systems, such as the latest Android versions and iOS.
Here’s a guide for how to encrypt your Android device, one for iOS and one for Windows Phone.

Hope you also have an antivirus product installed on your PC. If your PC is infected with a virus and you connect your phone to it via USB, then your phone will also be infected.
And since we brought up this subject: don’t connect your smartphone to unknown computers. They might be infected with malware and end up infecting your mobile too.
Use your mobile data instead – it will cost you more, but your data won’t be at risk anymore.
A VPN can also protect you – that’s short for Virtual Private Network, a network created to protect your activity, that will encrypt your internet traffic and data. You can easily set up a VPN on today’s smartphones.
You should also keep your Bluetooth turned off – it’s not a secure way to communicate. Enable it only when necessary.

This way you’ll wipe all the data that was stored on it, including access to your accounts, system and app data and settings, downloaded apps, photos, music or any other data.
What’s important is the way you put to use that technology, that smartphone, that laptop, that tablet. The everyday usage habits.
Kevin Mitnick, one of the most well known security experts of our days, said that:
On one side, there are the ones who don’t even care about this issue. They aren’t aware of the potential vulnerabilities they expose themselves to. They can’t imagine why would anyone want to breach into their smart-phone or what can be done with their data. They’ve never even given a thought on how valuable is the data accessible through their phones and what would happen if it got leaked to their business competitors, sold or simply deleted.
Here are some scary statistics that might make them rethink the way they use their phones:
“67% of organisations had a data breach as a result of employees using their mobile phones to access the company’s data.”And then there are the ones under the illusion that, in order to be protected and untraceable while using your phone, they should give up on their comfort and convenience.
They are convinced that, if you want privacy and security, you can only achieve that either by using a burner, tons of layers of firewalls and proxies, or one of those new (and expensive) phones that focus on strong encryption.

It’s true that lately there’s been a market invasion of phones and apps that promote themselves as enhancers of your protection and security.
While we applaud the initiative, we should also point out that cyber security education is also very important. If you don’t set up some essential security layers, you’ll be extremely vulnerable on any phone you use, no matter its brand or operating system.
What it’s important is that you know how to properly use that phone and create some basic security habits in order not to expose yourself.

After they purchase a new phone, most people don’t even take their time to check all the existent settings.
Yes, it’s a shame that some of them aren’t activated by default. Things like two-factor authentication and automated screen-lock should be imposed by companies, and not offered only as optional settings.
However, basic security settings for smartphones can be tweaked by anyone, without any advanced tech skills, to enforce some much needed security layers.
This is exactly what we plan to show you in this article: an essential list of things that you can do right now in order to keep your smartphone and data safe.
Let’s go!
Smartphone security guide – the easiest way to keep your phone & data safe
1. First layer of protection: activate a screen lock.
Activate a screen lock – after a short period of inactivity (30 seconds, for example), your phone should auto-lock itself. It’s a must not only for your mobile device, but also for your laptop or tablet. This is the easiest way to keep intruders away.It’s also essential that you enforce automatic wiping of the device after 10 failed login attempts.
The reason behind this is that you can never know where you’ll accidentally forget your phone and who will end up accessing it. No matter how protective you are with it, there’s no guarantee that it won’t end up stolen one day.
You can simply leave it on your table while in a bar or at work for a quick break, and someone will peek into it. Or, even worse, install a keylogger or screen recorder on it.
Yes, you may currently vouch for your friends and work colleagues and jump into fire for them, but you can never know if that trust is mutual or how your relationship will evolve. Are you willing to take that chance?
Six years ago, I got burned because of my naivety. An employee I had just fired wanted to get revenge, so he hacked into my website and personal accounts and did as much harm as possible. While he was still employed, he managed to install a keylogger on my laptop – laptop I left unattended and without any screen lock on it, thus making all my other security layers useless. Now that I’m looking back at what happened, I feel stupid. Learn from my mistakes!

And now, moving on to the details: don’t use a PIN code for locking the screen. That’s the easiest one to breach, someone just has to be peeking while you unlock your phone.
Instead, treat your screen lock just like you treat any other password: use a unique password, that’s long enough and mixes letters with digits and symbols.
Another option to lock your screen is using a pattern. Choose a complicated one and then deactivate the option that makes it visible when you enter it.
You can also use your fingerprint to wake and unlock your phone, in addition to the pattern, if you have it as an option. Here’s how you set it up in Android (click on the screenshots to enlarge them):

Biometrics are one of the most secure ways of authenticating oneself, and not because of its secrecy, but because it’s so difficult to replicate the data. While we do leave our fingerprints everywhere, it’s much easier for someone to spy on you from behind your shoulder while you enter your PIN than try to replicate your fingerprints.
And looks like biometrics are quickly gaining ground in the mobile world. The company Mastercard is working on a system that will allow us to pay with our faces.
Literally, all we’ll need to do to confirm a payment is take a selfie through a special app and blink while we do it. The blink will be a way to prevent fraud and illegal payments done with our photos, for example. We’ll most likely hear more details about it soon – the due date for starting to implement this option is summer of 2016.

2. Second layer of protection: mind your apps.
In the past decade, there were huge innovations regarding the mobile phone market. Now basically everybody owns a smartphone and it’s also incredibly accessible to create a mobile app.In the same time, security stagnated and just couldn’t keep up. Companies are focused more on marketing than on protecting their user’s data. They don’t care about proactive security and are willing to invest in it only when something bad happens.
Cases of smartphones that got infected with viruses and malware have been on a rise. Some of them ended up with annoying adware, while others were infected with ransomware:
“[…] in 2015 there was a 500% increase in the instances of smartphone users being targeted by so-called ransomware, with cybercriminals using exploitative apps to con money from users, in exchange for restoring full functionality to a device.”(source)
The Apple ecosystem is extremely targeted by cyber crooks, as iPhone owners are considered to be more wealthy and likely to pay a ransom. And because of their centralized system, a security vulnerability can affect a bigger percentage of the users base.
However, devices with iOS are generally considered to be safer than Android because of two main reasons:
1. Market fragmentation: Google allowed every phone manufacturer to personalize its own Android version. While this is also a strength, it’s also harder to control the security for every device that runs on Android, exposing users more to potential bugs.
2. Google is also more permissive with the apps that they allow in their official store. Unlike Apple, Google doesn’t check as thoroughly the apps that they allow users to install.
Of course, this is just a simplified view of the two biggest operating systems existent in the mobile market at this point. They both have their advantages and disadvantages when it comes to cyber security.
What you should keep in mind is that bugs and vulnerabilities will always exist, no matter what operating system you use. What’s important is the way you use it and what privacy layers you enforce.

Here’s what you can do about apps in order to decrease your chances to be infected:
Always use official app stores to download and install an app. Disable the option to allow installation of third party apps. Third party apps usually carry malware that will harm your smartphone. Is that a risk worth taking?
Only install applications that you find in the official app store. That means no apps from third parties – no matter if those third parties are your online buddies, ads, blogs or torrents.
If you have Android, you can disable the option to allow installation of apps from sources other than the Play Store (from Settings -> Security – screenshot below, you can click on it to enlarge it).

However, this doesn’t mean that an app or game from the official store is 100% secure – sometimes, even popular apps, with more than 5 million downloads, can prove to be infected.
Also check the permissions for the installed apps (here’s how to do it). If anything looks out of order, then deny them access to what they’re requesting. A flashlight app doesn’t need permission to access your text messages or contacts, right?
If you have Android, you can go to Settings -> Apps -> App permissions and check exactly what apps required permissions:

Or you can individually check permissions granted for each app: go to Settings -> Apps and scroll through the list of apps, click on one and individually check what permissions they requested and what you gave them access to:

Or here’s a helpful tool that can ease that task for you: Clueful is a free mobile app developed by Bitdefender that takes a look over what permissions are requested by each app and warns you of the potential threats.
Do a spring cleanup of your apps. Take a look over all the installed apps and remove the ones you’re not using anymore. Those are potential security risks and it’s better to be safe than sorry.
You should also check out the apps that consume the most battery, data or memory, to see if there’s anything suspicious around there. Look for significant changes – this way, you can detect if your smartphone has been compromised.
Update your apps. With each app that remains outdated, including commonplace browsers, your phone is more vulnerable to infections. All it takes is clicking on a link that will redirect you to an infected website – it can be a link from an ad, a spam email, or your friend’s social account that got hacked. Outdated apps leave your data exposed to attacks.
This free step by step smartphone security guide covers all the basics:
3. Third layer of protection: be careful with that web browsing.
Install an ad blocker. No, not because ads are intrusive and have been failing potential customers, but because they can be exploited by cyber criminals. Malvertising can be served right on your smartphone through ad servers – and you don’t even need to click on anything in order to get infected!A few weeks ago, a massive Angler malvertising campaign hit major websites, such as The New York Times, BBC, AOL. An ad block software will help decrease your chances of infection.
Blocking pop-ups will also help – you can easily do that from the browser settings. For Chrome, for example, you just have to go to Settings -> Site Settings -> Pop-ups -> and make sure it’s on Blocked.
It’s also recommended that you disable JavaScript for your mobile browser.
This will also help you reduce the data you consume: according to recent studies, ad content is accountable for between 18 to 79% of transferred mobile data. That’s especially true if you navigate through a lot of news websites.
“JavaScript elements – often used by publishers for ads, but also for visual elements such as animations – added an extra 6% to 68%. Enders noted that the JavaScript it came across in the study wasn’t central to the articles being loaded.”And last but not least, watch out for where you tap over your screen, be careful not to end up clicking by mistake where you didn’t want in the first place. Ads can be placed close to legit content and you can accidentally end up clicking on them.

4. Fourth layer of protection: beware of phishing.
It’s much harder to spot a phishing page on your mobile phone than on your PC or laptop.Keep your guard up against phishing on all your devices, no matter if it’s a desktop, laptop, tablet or smartphone. No clicking on short, suspicious links, that you didn’t request. And be careful with those attachments you download via email or instant messaging services.
Cyber attackers can use phishing techniques to withdraw money from you, steal your identity, open credit card accounts in your name and much more. Not even the strongest antivirus will protect you from phishing and malware.
A recent mobile threat is Mazar BOT – a virus that our team detected back in February. It’s spread via links sent in text messages and can give an intruder administrator rights on the victim’s phone. This allows the attackers to read, send and receive SMS, call people, and even erase the phone.
That’s why it’s important that you don’t click on links that you never requested and don’t know where they lead (especially short, hidden links). If somehow you end up clicking on them and they require you to sign-in, don’t give away your credentials.
Do you remember the Fappening, the huge scandal from the summer of 2014? Lots of pics (especially naked ones) with celebrities were stolen from their phones and leaked online. One of the attackers involved pleaded guilty for the attack. His method to access celebrities’ phones? Plain old email phishing:
“From the court documents, it became clear that the victims of Collins’ attack fell prey to a phishing scam. Collins allegedly sent e-mails to the victims that appeared to come from Google or Apple, warning the victims that their accounts might be compromised, and asking for their login details. The victims would enter their password information. Having gained access to the e-mail address, Collins was able to download e-mails, and get further access to other files, such as iCloud accounts.”Take your time and read our anti-phishing guide – it will help you detect and prevent the techniques used by cybercriminals.

5. Fifth layer of protection: activate remote device locator.
In case your smartphone is ever lost or stolen, the easiest way to remotely locate it is by installing a dedicated app and making sure that the option to track its location is always turned on.For iOS there’s the tracking solution called “Find my iPhone”, Microsoft has “Find my phone”, and Android has “Android Device Manager”.
Here’s how Android Device Manager looks like:

6. Sixth layer of protection: activate automatic backup.
Have automatic backups in cloud.This option is available on all operating systems, you just have to enable it (or don’t disable it, in case it’s already set as default).
In case that your phone is lost, destroyed or stolen, you won’t have to worry about the fact that you didn’t get the chance to backup all your data on it. All apps and data will be automatically synchronized in the cloud.
Here’s how you activate backup in Android (to backup your Photos you’ll have to go in the Photos app and configure it separately – you can choose what folders to backup and at what size to upload the photos):

“According to records submitted to the National Assembly by mobile carriers, 2.35 million mobile phones were lost in 2014 and only 1.26 million returned to their owners.”(source)
When you’ll set up a new device, you’ll just have to enter the credentials for your Apple or Google account, and all apps, settings and data will be automatically restored.
You can also set up your data to automatically backup in other accounts, such as Dropbox.
If you don’t want to quickly exhaust the internet traffic included in your data plan, set it up to backup only when it connects to wi-fi.

7. Seventh layer of protection: activate two-factor authentication.
No matter if you have an Apple, Google or Microsoft account, activating the two-factor authentication is a must.This will act as a second layer of security. Every time you’ll want to sign in on a new device or from a new location, it will require you to verify your identity through a unique, time sensitive code, that you’ll receive via text message.
In case you travel a lot and your phone is unavailable, you’ll be able to use backup codes instead. These are codes that you can use only one time.
Yes, it’s important that you use different passwords for all your accounts. However, in case that someone manages to steal your phone, access it and find out your password, they won’t be able to get through this second step of authentication.

8. Eighth layer of protection: turn on encryption.
If your smartphone offers the option to encrypt the data on it, enable it.Google explains how encryption works for Android:
“Full disk encryption is the process of encoding all user data on an Android device using an encrypted key. Once a device is encrypted, all user-created data is automatically encrypted before committing it to disk and all reads automatically decrypt data before returning it to the calling process.”Once you encrypt it, the phone will ask you to set a password to unlock it and decrypt the data on it. If you forget it, only a complete factory reset will get access back into the system.
Unfortunately, the option to encrypt your data is available for a limited number of operating systems, such as the latest Android versions and iOS.
Here’s a guide for how to encrypt your Android device, one for iOS and one for Windows Phone.

9. Ninth layer of protection: install an antivirus.
Install a trustworthy antivirus. Although they aren’t as potent as their desktop versions, it’s still a better alternative than having no antivirus installed.Hope you also have an antivirus product installed on your PC. If your PC is infected with a virus and you connect your phone to it via USB, then your phone will also be infected.
And since we brought up this subject: don’t connect your smartphone to unknown computers. They might be infected with malware and end up infecting your mobile too.
10. Tenth layer of protection: use a secure connection.
Only use secure wireless connections. That means no free or public wi-fi, especially when you’re accessing sensitive data (yes, we’re talking about that Starbucks connection. And the airport wi-fi also falls under this warning!). Information sent via public networks can be accessed by anyone who knows how to view it.Use your mobile data instead – it will cost you more, but your data won’t be at risk anymore.
A VPN can also protect you – that’s short for Virtual Private Network, a network created to protect your activity, that will encrypt your internet traffic and data. You can easily set up a VPN on today’s smartphones.
You should also keep your Bluetooth turned off – it’s not a secure way to communicate. Enable it only when necessary.

11. Eleventh layer of protection: have a Factory Data Reset.
If you’re planning on selling your phone, make sure you don’t forget to do a Factory Data Reset before you give it away.This way you’ll wipe all the data that was stored on it, including access to your accounts, system and app data and settings, downloaded apps, photos, music or any other data.
Conclusion
Just because you don’t have a state of the art phone or the latest operating system, it doesn’t mean that you can’t keep it safe.What’s important is the way you put to use that technology, that smartphone, that laptop, that tablet. The everyday usage habits.
Kevin Mitnick, one of the most well known security experts of our days, said that:
“It’s much easier to hack a human than a computer because computers follow instructions, they don’t vary – humans go by emotion, by what’s happening in their day… so it’s not hard” to socially engineer someone – “especially if they haven’t been burned before.” […] Hackers will take advantage of the fact that people are lazy. […] The best defense against phishing isn’t antivirus or firewall software per se, but training, education and awareness.”




0 comments